Protect your documents with Digital Signature and KGpg

Transferring files or digital documents from one computer to the other also means exposing them to risks, these documents could be intercepted. It doesn’t matter what method you use to transfer these documents, via Ftp, Samba, Email, NFS etc if it’s not well protected an intruder could pick it up. What if the intruder gets directly to your computer? What can be done to prevent someone from owning our documents?
We can use the PGP (Pretty Good Privacy) system. Its open source counterpart that I’m going to present to you is called GPG (Gnu Privacy Guard). This software is installed by default on all GNU/Linux distros and contains all that’s necessary to encrypt, decrypt, and to digitally sign a document or file. Unfortunately to use GPG from the command line is quite difficult so we’ll adopt KGPG that has a graphic interface and is integrated on the KDE Desktop.
Look at this sketch to understand what Digital Signature is all about.
Generating a New Key Pair
To run KGpg, open the K menu and click on Accessories, PIM, KGpg or kgbg on the command line. Go directly to the key generation menu and generate the “public/private key pair. The Public key can be given to anyone(friends, co-workers etc) while the Private key should be kept secret.

Exporting the Public Key
After generating your key pair, make the public key available to other users. This enables them to use it to encrypt or sign the messages or files they send you. To make the public key available for others, select Keys+Export Public Key(s) and choose one of the four options: ‘Email’, ‘Clipboard’, ‘Defualt Key Server’ and ‘File’
Importing Keys
If you receive a key in a file (for example, as an e-mail attachment), integrate it in your key ring with Import Key… and use it for encrypted communication with the sender. The procedure is similar to the procedure for exporting keys already described.
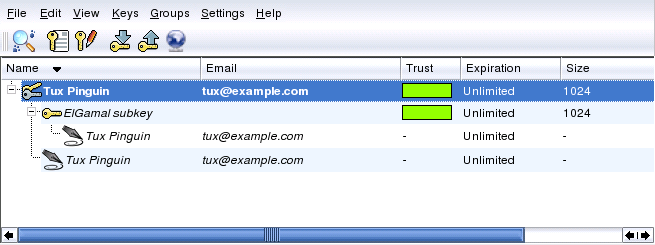
How secured are the Keys.
After creating the pair of keys and secured it with a password, all the public keys that we have and their Trust level would be shown. Our Trust level would be in green, for others in white, so we would not able to see the owners of the other keys. This means that the keys created by us are effectively ours, but on the other hand if a digitally signed email is sent to us by a friend, containing a public key, how do we get to know if he is the one who effectively sent to us the mail or it’s a fake. So the keys sent to us by our contacts are untrusted. Thus, we have to place a high level of Trust only to those key that are given to us privately.